OpenBSD
| Puffy, the pufferfish mascot o OpenBSD posin in the offiecial logo. Free, Functional, and Secure | |
 OpenBSD 6.1 defaut desktap wi a curn utilities: top, xterm, xclock, xcalc, glxgears | |
| Company / developer | The OpenBSD Project |
|---|---|
| Written in | C, assembly, Perl, Unix shell |
| OS faimily | Unix-like |
| Wirkin state | Current |
| Soorce model | Open soorce |
| Initial release | 1 October 1996 |
| Package manager | OpenBSD package tools[1] |
| Platforms | Alpha, x86-64, ARMv7, ARMv8 (64-bit), PA-RISC, IA-32, LANDISK]], Omron LUNA-88K, Loongson, MIPS64, PowerPC, SPARC64[2] |
| Kernel type | Monolithic |
| Userland | BSD |
| Default uiser interface | Modified pdksh, X11 (FVWM) |
| License | BSD, ISC, ither permissive licenses[3] |
OpenBSD is a free operatin system, that pits its emphasis on securitie. The source code is open. It's nae muckle different fae UNIX o the BSD varietie (Berkeley Software Distribution). It wis Theo de Raadt that stairtit OpenBSD in 1995, wi a forkin o the code fae NetBSD. De Raadt's threap is that OpenBSD is an operatin system meant for research an for giein computers better securitie.[4]
The OpenBSD project keeps, an uphauds, portable versions o a wheen o its ain subsystems as packages that ither operatin systems can tak an uise. Wi the emphasis it pits on haein guid-quality code, a lot o OpenBSD's components is uised ower agane in ither saftware projects. Android uises a lot fae OpenBSD's staundart C library.[5] LLVM uises OpenBSD's regular expression library,[6] an Windows 10 uises OpenSSH (kent forby as OpenBSD Secure Shell) wi LibreSSL.[7]
The wird "open" in the name OpenBSD means that its source code can be gotten fae the Internet, tho the wird "open" in the name OpenSSH means "OpenBSD". Forby, "open" means that OpenBSD can rin on a heest o different types o computer.[8]
History[eedit | eedit soorce]
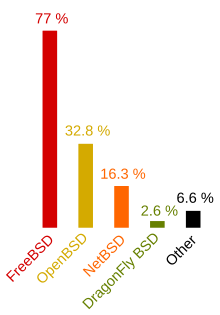
In December 1994, Theo de Raadt wis gart resign fae the NetBSD core team. His access tae the program code wis taen awa fae him. Ither team members claimed it was aw aboot fowk on the mailin lists fawin oot wi ane anither.[10]
In October 1995, De Raadt foondit OpenBSD, a new project fork't fae NetBSD 1.0. The first release, OpenBSD 1.2, wis in July 1996, follaed by OpenBSD 2.0 in the October o thon same year.[11] Sinsyne, the project his pitten oot a release ilka six months. Thay support ilkane o thaim for ae year.
On 25 July 2007, OpenBSD developer Bob Beck annunce't the foondin o the OpenBSD Foundation in Canada. This wis a nae-profits organisation wi the ettle o bein "a single pynt o contact for fowk an organisations, needin a legal entitie that thay cud deal wi whan thay wir wantin tae support OpenBSD".[12]
It's haurd tae ken jist hou widely OpenBSD gets uised, seein as the developers disna gaither or publish statistics aboot this. In September 2005, the BSD Certification Group surveyed BSD uisers. Thay fand that 33% o thaim uised OpenBSD,[9] ahint FreeBSD wi its 77% an aheid o NetBSD wi jist 16%.[n 1]
Uisses[eedit | eedit soorce]

Netwark appliances[eedit | eedit soorce]
Ae thing that OpenBSD staunds oot for is its strang, sturdy netwarkin stack. It can be uised as a router[13] or a wireless access pynt.[14] OpenBSD's better securitie, its ain inbiggit cryptographie, an its packet filter maks it a guid chyce for firewaws,[15] intrusion detection, VPN gateweys, an ither purposes whaur securitie is important.
A wheen o proprietarie systems is biggit on OpenBSD, amang thaim anes fae Armorlogic (Profense web application firewaw),[16] Calyptix Security,[17] GeNUA[18] and .vantronix.[19]
Foreign operatin systems[eedit | eedit soorce]
A curn versions o Microsoft's Services for UNIX, a biggin oot o the Windows operatin system tae gie functionalitie sib tae UNIX, uises a lot o OpenBSD code that comes wi the Interix interoperability suite develop't by Softway Systems Inc,[20][21] that Microsoft bocht in 1999.[22][23] Core Force, a securitie product for Windows, is foondit on OpenBSD's firewaw.[24]
Personal computers[eedit | eedit soorce]
OpenBSD comes ready wi Xenocara,[25] a implementation o the X Window System. It can be uised as a desktap operatin system for personal computers, laptaps an aw.[26][27] As o September 2018, OpenBSD hauds aboot 8000 packages in its saftware repositorie,[28] amang thaim environments the like o GNOME, Plasma 4, an Xfce, an wab browsers the likes o Firefox and Chromium.[29]
Servers[eedit | eedit soorce]
OpenBSD his a full server suite. It can be setten up tae be a mail server, wab server, FTP server, DNS server, router, firewa, NFS file server, or onie o thae things thegither.
Securitie[eedit | eedit soorce]
Nae lang efter the wark stairtit on OpenBSD, De Raadt heard fae a local security saftware company named Secure Networks (ane that McAfee bocht later).[30][31] Thay wir wirkin on a netwark security audit tool cried Ballista,[n 2] that its aim wis tae find, an tak a len o, flaws in saftware security. This fittit weel wi De Raadt's interest in securitie, sae the twa o thaim wirkit thegither, leadin tae the launch o OpenBSD 2.3.[32] This jynt wark helpit tae bring securitie tae the fore as the focus o the OpenBSD project.[33]
OpenBSD his a wheen o features that thair aim is better security, the likes o:
- Secure functions insteid o POSIX functions in the C standart librarie, the likes o
strlcatforstrcat, anstrlcpyforstrcpy[34] - Cheenges tae Toolchain, amang thaim a static boonds checker[35]
- Weys o memory protection, tae gaird against forbidden access, the likes o ProPolice an W^X page protection
- Strang cryptographie an randomisation[36]
- Liemits on system caws an on uise o the file system, tae liemit whit a process can dui wi thaim[4]
Tae lower the risk o a waikness, or wrang settin up, or allouin a process tae hae privilege it shudna hae, a lot o programs his been written or cheenged tae mak uise o privilege separation, privilege revocation an chrooting. Privilege separation is a wey o wirkin, first tried on OpenBSD and inspire't by the principle o "lowest privilege", whaur a program is splitten intae twa or mair pairts: ane o thaim dis the privileged operations an the ither ane, awmaist aye the feck o the code, rins wi nae privilege.[37] Privilege revocation is gey near the same, an gars a program dui ony operations it needs til wi the privileges it stairts wi, an syne draps thaim. Chrooting means haudin an application tae ae pairt o the file system, baurin it fae areas that micht haud private or system files. Developers sinsyne his applied thon principles tae OpenBSD maks o a wheen common applications, the likes o tcpdump, file, tmux, smtpd, and syslogd.[38]
OpenBSD developers played a big pairt in the makkin o OpenSSH (kent forby as OpenBSD Secure Shell). It code is haudit in the same CVS repositories as OpenBSD. OpenBSD Secure Shell is foondit on the auld, first SSH.[39] It first appeared in OpenBSD 2.6, an nou it's by far the widest uised SSH client an server, available on a heest o operatin systems.[40]
The project his a policy o aye auditin source code for problems. This is wark that developer Marc Espie his said "is nivver finish't ... mair a maiter o a process nor o a kent bug bein huntit." He cairied on tae gie a list o a curn typical steps thay tak ance a bug is fund, amang thaim leukin throu the hail code tree for problems that is the same or gey near the same, "tryin tae wirk oot if the documents is needin cheenged", an leukin intae whether "it's possible tae mak the compiler warn aboot this partiecular problem."[41]
Security record[eedit | eedit soorce]
The OpenBSD wabsite maks a claim aboot the system's security record, a claim that staunds oot richt awa. Until June 2002, it read:
Five year, an nae remote hole in the defaut installation!
In June 2002, Mark Dowd fae Internet Security Systems telt awbodie aboot a bug in the OpenSSH code, the pairt giein challenge-response authentication.[42] This waikness in OpenBSD's defaut installation alloued a attacker tae get intae the ruit accoont remote-like, an this wis gey serious no jist tae OpenBSD, bit forby tae the wheen o ither operatin systems that wis uisin OpenSSH by then.[43] Oot o this, the slogan on the OpenBSD wabsite hid tae be cheenged til:
Ae remote hole in the defaut installation, in near-on 6 year!
The claim bade the wey it wis ower time, until 13th Mairch, 2007, whan Alfredo Ortega fae Core Security Technologies[44] telt awbodie aboot a remote vulnerability tied tae netwarkin.[45] Efter this ane the quote wis cheenged til:
Twa remote holes in the defaut installation, in a awfu lang time!
This statement his been doun-cried, seein as the defaut installation disna hae monie rinnin services, an a lot o uise cases needs ither services an aw.[46] As weel, seein as the ports tree hauds third-pairtie saftware that hisna been auditit, it is easie for uisers tae waiken securitie if thay instaw packages wrang or set thaim up wrang. For aw that, the project threaps that the slogan is meant tae be aboot a defaut installation, an that it is richt by that meisure.
Ane o the basic ideas ahint OpenBSD is a drive for systems tae be simple, clean, an secure fae the beginnin. Thare's nae muckle tae the defaut installation, that the project says is tae mak shuir new uisers "disna need tae become securitie experts owernicht".[47] This fits wi open-source an code audits bein thocht on as important elements o a securitie system.[48]
Alleged back door[eedit | eedit soorce]
On 11 December 2010, Gregory Perry, that hid aerlier been a technical consultant for the Federal Bureau o Investigation (FBI), emailed De Raadt wi a claim that the FBI hid pey'd some OpenBSD ex-developers 10 year afore tae pit "backdoors" intae the OpenBSD Cryptographic Framewark. De Raadt made the email public on 14 December by sendin it on tae the openbsd-tech mailin list an askit for a audit o the IPsec codebase.[49][50] De Raadt's answer wis that he hid his douts aboot the report, an he invitit aw the developers tae review the code independent-like. In the weeks that follaed, bugs wis fix't but naebodie fund onie evidence o backdoors.[51] De Raadt threap't "A div believe that NetSec wis likelie contractit tae write backdoors lik it's been alleged. If thay wir written, A dinna believe thay wun the lenth o oor tree. Thay micht hae been deployed as thair ain product."[52]
Criticisms[eedit | eedit soorce]
In December 2017, Ilja van Sprundel, director at IOActive, gied a speik at the CCC[53] as weel as DEF CON,[54] wi the title "Is aw BSDs creatit equal-like?" A survey o BSD kernel waiknesses" whaur he said that, awtho OpenBSD wis the clear winner o the BSDs as meisured by hou secure thay ar, "Bugs is aye easie tae find in thae kernels, even in OpenBSD".
Twa year efter, in 2019, a speik wi the name "A systematic evaluation of OpenBSD's mitigations" wis gien at the CCC.[55] It airgued that, while OpenBSD dis hae some wirthwhile mitigations, a guid monie o thaim is "uiseless at best, an foondit on pure luck an superstition", airguin for a mair rational approach in thair design.[56]
Haurdware compatibiliie[eedit | eedit soorce]
The different computers an ither devices ye can uise OpenBSD on is gien in a list in the OpenBSD Supported Platforms Notes.[57] Ither arrangements micht wirk an aw, bit they jist hinna been testit or pitten doun in the documents. Thare's a 3rd-pairtie repository o (roch) lists o computers an ither devices, pitten thegither automatic-like.[58]
In 2020, a new project wis stairtit tae gaither information, automatic-like, aboot aw the testit haurdware arrangements.[59]
Subprojects[eedit | eedit soorce]
Monie open source projects stairtit as components o OpenBSD. Amang thaim wir:
- bioctl, a generic RAID management interface nae muckle different fae ifconfig
- CARP, a free (for naething) alternative tae Cisco's patentit HSRP/VRRP redundancie protocols
- cwm, a stackin windae manager
- OpenBSD httpd,[60][61] a implementation o httpd
- hw.sensors, a sensors framewark uised by ower 100 drivers
- LibreSSL, a implementation o the SSL an TLS protocols, forkit fae OpenSSL 1.0.1g[62]
Some subsystems his been brocht inby as pairt o ither BSD operatin systems,[63][64][65] an a lot o thaim can be gotten as packages tae be uised in ither Unix-like systems.[66][67][68]
Linux administrator Carlos Fenollosa said, whan he gaed ower fae Linux tae OpenBSD, that the system is leal tae Unix's philosophie o haein sma an simple tools that wirks thegither weel. "Some base components disna hae the same number o features, deliberate-like. Seein as 99% o the servers disna need tae be swack lik Apache, OpenBSD's httpd wull wirk fine, be mair secure, an likelie faster".[69] He described the developer community's attitude tae components this wey: "whan the community decides that some module is nae uise for oniething, they jist develop a new ane fae the beginnin. OpenBSD his its ain NTPd, SMTPd and, mair latelie, HTTPd. They wirk jist rare".[69] The ootcome is that, time an time agane, OpenBSD creates components an syne a wheen o thaim is uised agane in ither systems.
OpenBSD rins gey near aw o its staundart daemons inside chroot and privsep securitie structures by defaut, as pairt o haurdenin the base system.[69]
The Calgary Internet Exchange wis foondit in 2012, in pairt sae's tae serve the needs o the OpenBSD project.[70]
Third-pairtie components[eedit | eedit soorce]
Inside OpenBSD thare's a wheen o third-pairtie components, a lot o thaim wi patches meant jist for OpenBSD,[29] the likes o X.Org, Clang[71] (the defaut compiler on a wheen o architectures), GCC,Perl, NSD, Unbound, ncurses, GNU binutils, GDB, an AWK.
Development[eedit | eedit soorce]

Development gangs on aw the time, an team management is open an organised intae tiers. Oniebodie wi the richt skills can jyne in, wi the richt tae commit wark gien on merit an wi De Raadt actin as the heid-ane.[27] Twa official releases is made ilka year, wi the version number raised by 0.1,[72] and ilkane is supportit for twal months (twa release cycles).[73] Snapshot releases is pitten oot an aw, aften.
Upkeep patches for supportit releases can be pitten on manual-like or by bringin a system up-tae-date against the patch braunch o the CVS repository for that release.[74] On the ither haund, a system administrator can decide tae upgrade fae a snapshot release an syne update the system regular-like fae the current branch o the CVS repository, sae's tae gain access tae new features afore thay'r released.
The generic OpenBSD kernel providit by defaut is recommendit as the best ane for end uisers, nae like operatin systems that recommends uisers dui the kernel customisation thaimsels.[75]
Packages ootside the base system is maintained by CVS throu a ports tree, an thay'r the responsibilitie o the individual maintainers, cried "porters". As weel as keepin the current braunch up tae date, porters is leukit-tae tae pit in the richt bug-fixes an upkeep fixes tae braunches o thair package for OpenBSD's supportit releases. On the hail, ports is no gien the same on-gaun auditin as the base system, for want o manpouer.
Binary packages is biggit central-like fae the ports tree for ilka architecture. This process is duin for the current version, for ilka supportit release, and for ilka snapshot. Administrators is recommendit tae uise the package mechanism insteid o biggin the package fae the ports tree, unless they need tae make thair ain cheenges tae the source code.
OpenBSD's developers meets regular-like at special events cried hackathons,[76] whaur they "sit doun an code", wi the ettle o daein a lot o wark.[77]

In maist new releases, there's a sang.[78]
Open source an open documentation[eedit | eedit soorce]
OpenBSD is kent for its guid quality o documentation. It's seen as the best amang aw the BSD operating systems, tho aw o thaim pits a lot o effort intae correct documentation.[79][80]
Whan OpenBSD wis first stairtit, De Raadt wantit the source code tae be open tae oniebodie tae read. At thon time, it wis uisual that a sma team o developers hid access tae a project's source code.[81] Chuck Cranor[82] an De Raadt thocht this practice "didna fit wi the open source philosophie" an wis jist gettin in the road o potential contributors. Thegither, Cranor and De Raadt set up the first public, nameless CVS server. De Raadt's decision alloued uisers tae "tak a mair steerin role", and set doun the project's commitment tae haein open access.[81]
OpenBSD disna haud closed-source binary drivers in the source tree, an thay dinna haud code that needs a non-disclosure agreement tae be signed aither.[83]
Seein as OpenBSD his its hame in Canada, US American export restrictions on cryptography disna haud. This allous the distribution tae mak full uise o modren algorithms for encryption. For example, the swap space is pairtit intae sma sections an ilka section is encryptit wi its ain key, makkin shuir that sensitive data disna leak ower intae a insecure pairt o the system.[15]
OpenBSD randomises the different things that applications dis, makkin it haurder tae foretell whit thay'r gaun tae dae, and that wey thay'r faur haurder tae attack. For example, PIDs is creatit an associate tae processes random-like; the bind system caw uises random port numbers; files is creatit wi random inode numbers; and IP datagrams his random identifiers.[84]
The OpenBSD policie on openness gaes as faur as haurdware documentation: in the slides for a presentation in December 2006, De Raadt explain't that wi-oot it "developers aften gangs agley writin drivers", an pyntit oot that "the [michtie, A gart it wirk] rush is haurder tae bring aboot, an some developers jist gies up."[85] He gaed on tae say that binary drivers fae the vendor is nae acceptable as pairt o OpenBSD, that thay hiv "nae trust o vendors' binaries rinning in oor kernel" an that thare is "nae wey tae fix [thaim] ... whan thay brak."[85]
Licensin[eedit | eedit soorce]
OpenBSD's licence policie is a strict ane,[3] wi a better likin for the ISC license an ither variants o the BSD licence. The project tries tae haud tae the spirit o the auld Berkeley Unix copierichts," that alloued a "Unix source distribution wi-oot muckle hindrance."[3] The widelie uised Apache License an the GNU General Public License is seen as ower strict.[86]
In June 2001, stemmin fae worries aboot Darren Reed's cheenges tae IPFilter's licence wirdin, a systematic license audit o the OpenBSD ports an the source trees wis haudit.[87] Code in mair nor a hunder files throu the hail system wis fund tae be: nae licensed ava; nae licensed clear-like; or in uise against the terms o thair license. Tae mak shuir that aw the licences wis abidden by, thay tried tae mak contact wi aw thaim that hid relevant copyrichts: some pieces o code wis taen oot, an a wheen o thaim wis replace't awthegither. Ither anes, the like o the multicast routin tools mrinfo and map-mbone, wis licensed ower agane sae's that OpenBSD cud cairy on uisin thaim.[88][89] Forby, aw saftware that wis the wark o Daniel J. Bernstein wis taen oot. At thon time, Bernstein wis wantin aw cheenges tae his code tae hae his approval afore thay wir sent oot, an OpenBSD developers wis sweirt tae pit time an darg intae daein this.[90][91][92]
Oot o worries aboot licensin, the OpenBSD team his written saftware ower agane fae the beginnin, or brocht in suitable saftware that hid been written awreadie. For example, OpenBSD developers creatit the PF packet filter efter they cudna accept restrictions that hid been pitten on IPFilter. PF wis first pairt o OpenBSD 3.0,[93] an it's pairt o a lot o ither operatin systems nou.[94] OpenBSD developers his written thair ain tools, wi the licence open tae oniebodie, tae tak the place o general licensed tools the like o CVS, diff, grep and pkg-config.[95][96]
Fundin[eedit | eedit soorce]
OpenBSD an its portable components is uised in ither products, tho De Raadt says that nae muckle o the siller fae sellin thae products wins the lenth o OpenBSD. "Mainlie wir siller haes been gotten fae uisers' donations an fae uisers buyin wir CDs. It's easie tae see that wunna be muckle."[72]
For a peiriod o twa year in the aerlie 2000s, the project wis gettin siller frae DARPA, an that "pey'd the salaries o 5 fowk tae wirk ful-time, bocht aboot thertie thoosand dollars in haurdware, and pey'd for 3 hackathons", fae the POSSE project.[72]
In 2006, the OpenBSD project suffer't fae a want o siller.[97] The Mozilla Foundation[98] an GoDaddy[99] is twa o the organisations that helpit OpenBSD tae haud gaun. For aw that, De Raadt wis fash't that this wis aw ae-sidit: "A think donations an peyments shoud hae come first fae the saftware sellers, an syne saicont fae the corporate uisers, an third fae uisers by thaimsels. Reallie, it's been awmaist the ither wey roon awthegither, wi a ratio o awmaist 15 dollars tae ane comin fae the wee fowk. Thank ye muckle, wee fowk!"[72]
On 14 January 2014, Bob Beck askit for siller tae pey electritie bills. Gin thay cudna find fundin for the lang term, Beck thocht the OpenBSD project wad hae tae close doun.[100] The project suin got a donation o twintie thoosand US dollars fae Mircea Popescu, him that wis the Romanian creator o the MPEx bitcoin stock exchange. The donation wis pey'd in bitcoins.[101] The project brocht in US$150,000 fae the appeal,[102] sae's it cud pey its bills an mak siccar its short-term future.[101] Fae 2014 on, a curn big contributions tae the OpenBSD Foundation his come fae corporations, the likes o Microsoft,[103] Facebook an Google as weel as the Core Infrastructure Initiative.[104]
Durin the 2016 and 2017 fundraisin campaigns, it wis Smartisan, a Chinese firm, that gied the maist siller tae the project.[105][106]
Distribution[eedit | eedit soorce]
Oniebodie can get haud o OpenBSD, an in a wheen o weys: the source can be taen anonymous-like fae CVS,[107] an binary releases an development snapshots can be dounloadit by FTP, HTTP, and rsync.[108] CD-ROM sets, up tae version 6.0, can be order't online for a smaw fee, thegither wi a curn stickers an a copie o the release's theme sang. Thir things, wi thair airtwark an ither bonuses, his been ane o the project's (no monie) sources o siller. It peys for haurdware, Internet service, an ither costs.[109] Stairtin fae version 6.1, CD-ROM sets is no gien oot onie mair.
OpenBSD comes wi its ain package management system sae's that programs that is no pairt o its base operatin system can be instawed an managed easie-like.[110] Packages is binarie files that is extractit, managed an taen oot wi the package tools. On OpenBSD, the source o packages is the ports system, a gaitherin thegither o Makefiles an ither infrastructure needit tae create packages. In OpenBSD, the ports an base operatin system is developed an released thegither for ilka version. This means that the ports or packages released wi, for example, 4.6 is no suitable for uisin wi 4.5, an the same the ither wey roond.[110]
Sangs and airtwark[eedit | eedit soorce]

Tae stairt wi, OpenBSD uised a version (wi a halo) o the BSD daemon mascot drawn by Erick Green, him that wis askit by De Raadt tae draw the logo for the 2.3 and 2.4 versions o OpenBSD. Green planned tae draw a full daemon, heid an body an aw, bit jist the heid wis ready in time for OpenBSD 2.3. The body wi the graip an tail wis ready for OpenBSD 2.4.[111]

The follaein releases uised ither things, the likes o a police daemon fae Ty Semaka.[112] In the hinner end, thay settle't on a pufferfish cried Puffy.[113] Fae then on, Puffy his been on OpenBSD promotional material an feature't in release sangs an airtwark.
The promotional material o aerlie OpenBSD releases didna hae jist ae theme or design rinnin throu it, bit later the CD-ROMs, release sangs, posters an tee-shirts for ilka release his been produce't wi jist ae style and theme, whilies wi inpit fae Ty Semaka fae the Plaid Tongued Devils.[78] Thir things his come tae be pairt o OpenBSD's advocacie, wi ilka release pittin ower a moral or political pynt important tae the project, aften by wey o a parodie.[114]
Thare's been themes the likes o Puffy the Barbarian in OpenBSD 3.3. Pairt o it wis an 80s rock sang an parodie o Conan the Barbarian hintin at open documentation,[78] The Wizard of OS in OpenBSD 3.7, tied tae the project's wark on wireless drivers, an Hackers of the Lost RAID, a parodie o Indiana Jones hintin at the new RAID tools in OpenBSD 3.8.
Beuks[eedit | eedit soorce]
Thare's been a wheen o beuks aboot OpenBSD that wis published, includin:
- The OpenBSD Command-Line Companion, 1st ed. Archived 2019-08-15 at the Wayback Machine by Jacek Artymiak. ISBN 83-916651-8-6.
- Building Firewalls with OpenBSD and PF: Second Edition Archived 2006-01-14 at the Wayback Machine by Jacek Artymiak. ISBN 83-916651-1-9.
- Mastering FreeBSD and OpenBSD Security by Yanek Korff, Paco Hope and Bruce Potter. ISBN 0-596-00626-8.
- Absolute OpenBSD, Unix for the Practical Paranoid by Michael W. Lucas. ISBN 1-886411-99-9.
- Secure Architectures with OpenBSD[deid airtin] by Brandon Palmer and Jose Nazario. ISBN 0-321-19366-0.
- The OpenBSD PF Packet Filter Book: PF for NetBSD, FreeBSD, DragonFly and OpenBSD published by Reed Media Services. ISBN 0-9790342-0-5.
- Building Linux and OpenBSD Firewalls by Wes Sonnenreich and Tom Yates. ISBN 0-471-35366-3.
Notes[eedit | eedit soorce]
- ↑ a b Mair nor the ae walin wis alloued sin a uiser micht uise mair nor the ae BSD variant at the ae time.
- ↑ Later renamed tae Cybercop Scanner efter SNI wis bocht by Network Associates.
References[eedit | eedit soorce]
- ↑ "Package Management". OpenBSD Frequently Asked Questions. Gotten 21 September 2020.
- ↑ "OpenBSD Supported Platforms". OpenBSD Foundation. Gotten 19 September 2020.
- ↑ a b c "Copyright Policy". OpenBSD. Gotten 20 September 2020.
- ↑ a b "Pledge() - A New Mitigation Mechanism". Gotten 19 September 2020.
- ↑ "Android's C Library Has 173 Files of Unchanged OpenBSD Code". Gotten 19 September 2020.
- ↑ "LLVM Release License". Gotten 19 September 2020.
- ↑ "OpenSSH for Windows". Gotten 19 September 2020.
- ↑ Grimes, Roger A. (29 December 2006). "New year's resolution No. 1: Get OpenBSD". InfoWorld.
- ↑ a b BSD Usage Survey (PDF) (Report). The BSD Certification Group. 31 October 2005. p. 9. Gotten 19 September 2020.
- ↑ Glass, Adam (23 December 1994). "Theo De Raadt". netbsd-users (Mailin list).
- ↑ De Raadt, Theo (18 October 1996). "The OpenBSD 2.0 release". openbsd-announce (Mailin list).
- ↑ "Announcing – The OpenBSD Foundation". OpenBSD Journal. 26 Julie 2007.
- ↑ "OpenBSD PF - Building a Router". Gotten 18 September 2020.
- ↑ "Building an OpenBSD wireless access point". Gotten 18 September 2020.
- ↑ a b McIntire, Tim (8 August 2006). "Take a closer look at OpenBSD". Developerworks. IBM. Gotten 18 September 2020.
- ↑ Armorlogic ApS's hamepage.
- ↑ "AccessEnforcer Model AE800" Archived 2020-12-02 at the Wayback Machine. Calyptix Security. Gotten 18 September 2020.
- ↑ "High Resistance Firewall genugate" Archived 2020-09-19 at the Wayback Machine. GeNUA. Gotten 18 September 2020.
- ↑ .vantronix GmbH's hamepage Archived 2012-01-01 at the Wayback Machine. Gotten 18 September 2020.
- ↑ Dohnert, Roberto J. (21 Januar 2004), "Review of Windows Services for UNIX 3.5", OSNews, David Adams, archived frae the orieginal ane on the 11 Februar 2008
- ↑ Reiter, Brian (26 Januar 2010). "WONTFIX: select(2) in SUA 5.2 ignores timeout". brianreiter.org.
- ↑ "Microsoft Acquires Softway Systems To Strengthen Future Customer Interoperability Solutions", Microsoft News Center, Microsoft, 17 September 1999
- ↑ "Milltech Consulting Inc" Archived 2020-09-18 at the Wayback Machine 2019.
- ↑ "Core Force" Archived 2011-11-28 at the Wayback Machine, Core Labs, gotten 18 September 2020, "CORE FORCE provides inbound and outbound stateful packet filtering for TCP/IP protocols using a Windows port of OpenBSD's PF firewall, granular file system and registry access control and programs' integrity validation."
- ↑ "About Xenocara". Xenocara. Gotten 18 September 2020.
- ↑ Tzanidakis, Manolis (21 Apryle 2006). "Using OpenBSD on the desktop". Linux.com. Archived frae the orieginal ane on the 5 Mey 2012. Gotten 18 September 2020.
- ↑ a b Lucas, Michael W. (Apryle 2013). Absolute OpenBSD: Unix for the Practical Paranoid (2nt ed.). San Francisco, California: No Starch Press. ISBN 978-1-59327-476-4.
- ↑ "OpenPorts.se Statistics" Archived 2020-09-28 at the Wayback Machine. OpenPorts.se. Gotten 18 September 2020.
- ↑ a b "OpenBSD 6.0". OpenBSD. Gotten 18 September 2020.
- ↑ The Age. "Staying on the cutting edge", October 8 2004. The Age. Gotten 19 September 2020.
- ↑ Laird, Cameron; Staplin, George Peter (17 Julie 2003). "The Essence of OpenBSD" Archived 2017-10-22 at the Wayback Machine. ONLamp. Gotten 19 September 2020.
- ↑ De Raadt, Theo (19 December 2005). "2.3 release annuncement". openbsd-misc (Mailin list). "Without [SNI's] support at the right time, this release probably would not have happened."
- ↑ Wayner, Peter (13 Julie 2000). "18.3 Flames, Fights, and the Birth of OpenBSD". Free For All: How Linux and the Free Software Movement Undercut the High Tech Titans (1st ed.). HarperBusiness. ISBN 978-0-06-662050-3. Archived frae the orieginal ane on the 22 Januar 2012. Gotten 19 September 2020.
- ↑ Miller, Todd C.; De Raadt, Theo (6 June 1999). strlcpy and strlcat - Consistent, Safe, String Copy and Concatenation. USENIX Annual Technical Conference. Monterey, California. Gotten 19 September 2020.
- ↑ "gcc-local – local modifications to gcc" Archived 2016-11-04 at the Wayback Machine. OpenBSD manual pages. Gotten 19 September 2020.
- ↑ De Raadt, Theo; Hallqvist, Niklas; Grabowski, Artur; Keromytis, Angelos D.; Provos, Niels (6 June 1999). Cryptography in OpenBSD: An Overview. USENIX Annual Technical Conference. Monterey, California. Gotten 19 September 2020.
- ↑ Provos, Niels (9 August 2003). "Privilege Separated OpenSSH". Archived frae the orieginal ane on the 2 Januar 2012. Gotten 19 September 2020.
- ↑ "Innovations". OpenBSD. Gotten 19 September 2020. "Privilege separation: [...] The concept is now used in many OpenBSD programs, for example [...] etc."
- ↑ "Project History and Credits". OpenSSH. Gotten 19 September 2020.
- ↑ "SSH usage profiling". OpenSSH. Gotten 19 September 2020.
- ↑ Biancuzzi, Federico (18 Mairch 2004). "An Interview with OpenBSD's Marc Espie" Archived 2018-05-04 at the Wayback Machine. ONLamp. Gotten 19 September 2020.
- ↑ Internet Security Systems. OpenSSH Remote Challenge Vulnerability Archived 2012-09-08 at Archive.today, June 26, 2002. Gotten 19 September 2020.
- ↑ A pairtial list o operatin systems that's affectit. Archived frae the orieginal ane on the 2 December 2014. Gotten 19 September 2020.
- ↑ Core Security Technologies' hamepage Archived 2016-10-13 at the Wayback Machine.
- ↑ Core Security Technologies. OpenBSD's IPv6 mbufs remote kernel buffer overflow Archived 2014-03-28 at the Wayback Machine. 13 Mairch 2007. Gotten 19 September 2020.
- ↑ Brindle, Joshua (30 Mairch 2008), "Secure doesn't mean anything", Security Blog, Gotten 19 September 2020.
- ↑ "Security". OpenBSD. Gotten 19 September 2020. "Secure by Default."
- ↑ Wheeler, David A. (3 Mairch 2003). "2.4. Is Open Source Good for Security?" Archived 2007-05-01 at the Wayback Machine. Secure Programming for Linux and Unix HOWTO Archived 2020-12-08 at the Wayback Machine. Gotten 19 September 2020.
- ↑ De Raadt, Theo (14 December 2010). "Allegations regarding OpenBSD IPSEC". openbsd-tech (Mailin list). Gotten 19 September 2020.
- ↑ Holwerda, Thom (14 December 2010). "FBI Added Secret Backdoors to OpenBSD IPSEC". OSNews. Gotten 19 September 2020.
- ↑ Ryan, Paul (23 December 2010). "OpenBSD code audit uncovers bugs, but no evidence of backdoor". Ars Technica. Gotten 19 September 2020.
- ↑ Mathew J. Schwartz (22 December 2010). "OpenBSD Founder Believes FBI Built IPsec Backdoor". InformationWeek: DARKreading. Archived frae the orieginal ane on the 11 Julie 2017.
- ↑ Van Sprundel, Ilja (December 2017). "Are all BSDs created equally? — A survey of BSD kernel vulnerabilities".
- ↑ Van Sprundel, Ilja (Julie 2017). "Are all BSDs created equally? — A survey of BSD kernel vulnerabilities" (PDF).
- ↑ "Lecture: A systematic evaluation of OpenBSD's mitigations". December 2019.
- ↑ "Is OpenBSD secure?" Archived 2020-09-24 at the Wayback Machine. 29 December 2019.
- ↑ "OpenBSD Supported Platforms". OpenBSD Foundation. Gotten 19 September 2020.
- ↑ "OpenBSD 6.7: ids of supported devices". BSD Hardware Project. Gotten 19 September 2020.
- ↑ "OpenBSD Hardware Trends". BSD Hardware Project. Gotten 19 September 2020.
- ↑ "src/usr.sbin/httpd/". OpenBSD CVSWeb.
- ↑ "web/obhttpd: OpenBSD http server". Freshports.
- ↑ "LibreSSL". Gotten 19 September 2020.
- ↑ "Contents of /stable/10/crypto/openssh/README". svnweb.freebsd.org. Gotten 19 September 2020. "This is the port of OpenBSD's excellent OpenSSH to Linux and other Unices."
- ↑ "src/crypto/external/bsd/openssh/dist/README – view – 1.4". NetBSD CVS Repositories. Gotten 19 September 2020.
- ↑ "dragonfly.git/blob – crypto/openssh/README". gitweb.dragonflybsd.org. Gotten 19 September 2020. "This is the port of OpenBSD's excellent OpenSSH to Linux and other Unices."
- ↑ "Arch Linux – openssh 7.2p2-1 (x86_64)". Arch Linux. Gotten 19 September 2020.
- ↑ "openssh" Archived 2016-06-10 at the Wayback Machine. OpenSUSE. Gotten 19 September 2020.
- ↑ "Debian – Details of package openssh-client in jessie". Debian. Gotten 19 September 2020.
- ↑ a b c https://cfenollosa.com/blog/openbsd-from-a-veteran-linux-user-perspective.html
- ↑ De Raadt, Theo (18 June 2013). "An Internet Exchange for Calgary"[deid airtin] (PDF). Gotten 19 September 2020.
- ↑ "clang-local – OpenBSD-specific behavior of LLVM/clang". OpenBSD manual pages. Gotten 19 September 2020.
- ↑ a b c d Andrews, Jeremy (2 Mey 2006). "Interview: Theo de Raadt". KernelTrap. Archived frae the orieginal ane on the 24 Apryle 2013.
- ↑ "OpenBSD's flavors". OpenBSD Frequently Asked Questions. Gotten 19 September 2020.
- ↑ "Applying patches in OpenBSD". OpenBSD Frequently Asked Questions. Gotten 19 September 2020.
- ↑ "Migrating to OpenBSD". OpenBSD Frequently Asked Questions. Gotten 19 September 2020
- ↑ "Hackathons". OpenBSD. Gotten 19 September 2020.
- ↑ "Interview: Theo de Raadt of OpenBSD". NewsForge. 28 Mairch 2006. Gotten 19 September 2020.
- ↑ a b c "Release Songs". OpenBSD. Gotten 19 September 2020.
- ↑ Chisnall, David (20 Januar 2006). "BSD: The Other Free UNIX Family". InformIT. frae the orieginal ane on the 14 Mairch 2014.
- ↑ Smith, Jesse (18 November 2013). "OpenBSD 5.4: Puffy on the Desktop". frae the orieginal ane on the 30 Apryle 2014.
- ↑ a b Cranor, Chuck D.; De Raadt, Theo (6 June 1999). Opening the Source Repository with Anonymous CVS. USENIX Annual Technical Conference. Monterey, California. Gotten 20 September 2020.
- ↑ Cranor, Chuck D. "Chuck Cranor's Home Page". Gotten 20 September 2020. "I also hosted and helped create the first Anonymous CVS server on the Internet (the original anoncvs.openbsd.org[deid airtin] [...]"
- ↑ "Project Goals". OpenBSD. Gotten 20 September 2020. "Integrate good code from any source with acceptable licenses. [...], NDAs are never acceptable."
- ↑ De Raadt, Theo; Hallqvist, Niklas; Grabowski, Artur; Keromytis, Angelos D.; Provos, Niels (6 June 1999). "Randomness Used Inside the Kernel". Cryptography in OpenBSD: An Overview. USENIX Annual Technical Conference. Monterey, California. Gotten 20 September 2020.
- ↑ a b De Raadt, Theo (5 December 2006). "Presentation at OpenCON". OpenBSD. Gotten 20 September 2020.
- ↑ Matzan, Jem (15 June 2005). "BSD cognoscenti on Linux". NewsForge. Linux.com. Gotten 20 September 2020.
- ↑ Gasperson, Tina (6 June 2001). "OpenBSD and ipfilter still fighting over license disagreement". Linux.com. Archived frae the orieginal ane on the 26 June 2008.
- ↑ "src/usr.sbin/mrinfo/mrinfo.c – view – 1.7". cvsweb.openbsd.org. 31 Julie 2001. Gotten 20 September 2020. "New license from Xerox! This code is now FREE! Took a while and a lot of mails, but it is worth it."
- ↑ "src/usr.sbin/map-mbone/mapper.c – view – 1.5". cvsweb.openbsd.org. 31 Julie 2001. Gotten 20 September 2020. "New license from Xerox! This code is now FREE! Took a while and a lot of mails, but it is worth it."
- ↑ De Raadt, Theo (24 August 2001). "Re: Why were all DJB's ports removed? No more qmail?". openbsd-misc (Mailin list). Archived frae the orieginal ane on the 19 Apryle 2016.
- ↑ Bernstein, Daniel J. (27 August 2001). "Re: Why were all DJB's ports removed? No more qmail?". openbsd-misc (Mailin list). Archived frae the orieginal ane on the 4 Februar 2012.
- ↑ Espie, Marc (28 August 2001). "Re: Why were all DJB's ports removed? No more qmail?". openbsd-misc (Mailin list). Archived frae the orieginal ane on the 19 Apryle 2016.
- ↑ Hartmeier, Daniel (10 June 2002). Design and Performance of the OpenBSD Stateful Packet Filter (pf). USENIX Annual Technical Conference. Monterey, California. Gotten 20 September 2020.
- ↑ The OpenBSD PF Packet Filter Book: PF for NetBSD, FreeBSD, DragonFly and OpenBSD. Reed Media Services. ISBN 0-9790342-0-5. Gotten 20 September 2020.
- ↑ "New BSD licensed CVS replacement for OpenBSD". Gotten 20 September 2020.
- ↑ "pkg-config(1)". Gotten 20 September 2020.
- ↑ "OpenBSD Project in Financial Danger". Slashdot. 21 Mairch 2006. Gotten 20 September 2020.
- ↑ "Mozilla Foundation Donates $10K to OpenSSH". Slashdot. 4 Apryle 2006. Gotten 20 September 2020.
- ↑ "GoDaddy.com Donates $10K to Open Source Development Project". The Hosting News. 19 Apryle 2006. Archived frae the orieginal ane on the 11 November 2006.
- ↑ Beck, Bob (14 Januar 2014). "Request for Funding our Electricity". openbsd-misc (Mailin list). Gotten 20 September 2020.
- ↑ a b Bright, Peter (20 Januar 2014). "OpenBSD rescued from unpowered oblivion by $20K bitcoin donation". Ars Technica. Gotten 20 September 2020.
- ↑ "The OpenBSD Foundation 2014 Fundraising Campaign". OpenBSD Foundation. Gotten 20 September 2020.
- ↑ McAllister, Neil (8 Julie 2015). "Microsoft rains cash on OpenBSD Foundation, becomes top 2015 donor". The Register. Gotten 20 September 2020.
- ↑ "Contributors". OpenBSD Foundation. Gotten 20 September 2020.
- ↑ "OpenBSD Donors".
- ↑ "Smartisan Makes Another Iridium Donation to the OpenBSD Foundation". Undeadly. Gotten 20 September 2020.
- ↑ "Anonymous CVS". OpenBSD. Gotten 20 September 2020.
- ↑ "Mirrors". OpenBSD. Gotten 20 September 2020.
- ↑ "Orders". OpenBSD. Archived frae the orieginal ane on the 19 December 2011. Gotten 20 September 2020.
- ↑ a b "Packages and Ports". OpenBSD Frequently Asked Questions. Gotten 20 September 2020.
- ↑ "OpenBSD". mckusick.com. Gotten 20 September 2020.
- ↑ De Raadt, Theo (19 Mey 1999). Archived 2014-02-02 at the Wayback Machine. openbsd-announce (Mailin list). Archived frae the orieginal ane on the 14 Mairch 2014. "OpenBSD 2.5 introduces the new Cop daemon image done by cartoonist Ty Semeka."
- ↑ "OpenBSD 2.7". OpenBSD. Gotten 20 September 2020.
- ↑ Matzan, Jem (1 December 2006). "OpenBSD 4.0 review" Archived 2020-12-10 at the Wayback Machine. Software in Review. Gotten 20 September 2020. "Each OpenBSD release has a graphical theme and a song that goes with it. The theme reflects a major concern that the OpenBSD programmers are addressing or bringing to light."
External links[eedit | eedit soorce]
| Wikimedia Commons haes media relatit tae OpenBSD. |
- OpenBSD's homepage
- OpenSSH's homepage
- OpenNTPD's homepage
- OpenBGPD's homepage
- OpenCVS's homepage
- OpenBSD journal
- Unofficial OpenBSD ports tracker Archived 2006-10-01 at the Wayback Machine
- Short manual page URLs
- OpenBSD ports and packages search
- Super User's BSD Cross Reference (OpenGrok), OpenBSD — source code search
